Architecture Weekly Issue #45. Articles, books, and playlists on architecture and related topics. Split by sections, highlighted with complexity: 🤟 means hardcore, 👷♂️ is technically applicable right away, 🍼 - is an introduction to the topic or an overview. Now in telegram as well.
WARNING 🇺🇦
It's already been 277 days since Russia's crazy, brutal, an unjustified war against Ukraine. We condemn this war and want it to stop ASAP. We continue this newsletter so you can advance your skill and help the millions of Ukrainian people in any way possible. If you want to help directly, visit this fund.
Video
Highlights
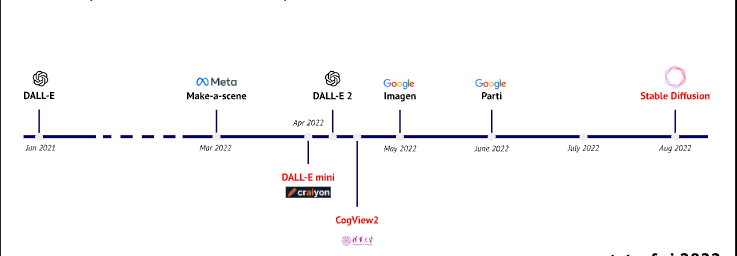
State of AI 2022 🍼
AI made a boom in social networks with text-to-picture engines, and - to a less extent - with Github Co-pilot. But the most interesting things happen below the level of public vision. State of AI Report highlights the amazing breakthroughs from the DeepMind team and other researchers. It also covers the regulations, hardware markets for AI, AI safety concerns and makes predictions for the next year. 100 pages of a report, but worth to click through.

#ai #ml
Policy in Continuous Delivery 👷♂️
This week Continuous Delivery Foundation introduced a new term - "Policy". With the growing complexity of software and delivery pipelines, some aspects can be done ad-hoc: like requiring a static code analysis step or forbidding rolling out changes on Christmas. In order to govern such restrictions CD pipelines would benefit from a single source of policies. Follow the article for the first tools which can provide such capability.

#cd #policy
Vulnerability Management at Lyft and fix cascade 👷♂️
Suppose, you find a vulnerability in a service; how to understand its impact? How to find out how it was introduced? How to fix it efficiently? Lyft shares its approach with cartography: mapping the connections between different entities in the first part of the article. The second part is the propagation of fixes across Docker images. Read the instruction inside!
#security
Follow-Up
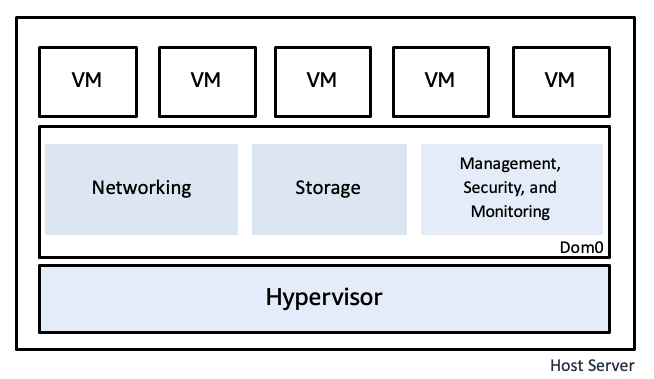
The security design of the AWS Nitro System 👷♂️
The software manages a lot of PII(Personal Identification Information), PHI(Personal Health Information) and PCI(Personal Commercial Information). Processing this data requires a high level of protection not only at the application but at the VM and hardware as well. AWS published a big material on how Nitro System works and how they provide a secure virtualization platform.
#aws #security
Google Cloud Platform security best practices 🍼
Once you setup a new project within a cloud provider, it's crucial to follow the best practices regarding security, like not doing anything with your root account, configure the rotation of the keys, enabling some defaults etc. In this post you fill find a long checklist of things you need to do in your GCP account before you deploy anything.

#gcp #cloud #security
Building a JSON CRDT 🤟
Paxos, Raft and other algorithms are a way to establish a consensus in a distributed system meaning there is only one true state of the data. What if we shift our understanding and say that every node of the system - including mobile and desktop clients - can have their own state? And that's why, if we demand that the state will eventually match if every node receives the same update. This is the idea behind CRDT - data types which allow building such a system. Read a long blog post which gives more details and shows how you can build such data type yourself.

#distributedsystem #crdt
Designing Embedded Software 🍼
Embedded Solutions bring new unobvious challenges to software architecture. Portability, Performance and Security are among them. Surprisingly, separation of concern works really well. Read the 2 articles from the series at embedded.com.
#architecture #portability #embedded
12 Factor App Revisited 🍼
Heroku was a popular platform to deploy apps to in the early 2010s. The founder of Heroku formulated 12 factors for the successful development of software as a service, from code repositories to managing logs. In this note, Mahdi Yusuf from "Architecture Notes" checks what changed in those 12 factors. Spoiler: the majority is still there, but an understanding of working with repositories and code storage definitely evolved.

#architecture #bestpractice
What is an Internal Developer Platform? 🍼
DevOps was a great idea: let's use some code to manage the infrastructure and run our services. However, the growing complexity of cloud services, technologies and approaches imposes a high cognitive load on developers. That's why the companies transition to the Developer Platform or Platform Engineering. This is what we do in Bolt as well: the developer only focuses on the business logic; the whole runtime is handled for him by a builder and runtime solution. Read, why this happens and why it's not a necessarily bad thing below.

#devops
5 diagramming tools for enterprise and software architects 🍼
This week I wrote a short article on diagramming tools. It is similar to what I wrote a year or so ago about 5 diagrams you only need to describe software architecture. But the peculiarity of this one is that it was a guest post on RedHat's blog. Read it too :)

#documentation
Have an article to suggest? Drop us a message!
Like the newsletter? Consider helping to run it at Patreon or Boosty. The funds go to pay for the hosting and some software like a Camo Studio license. Patrons and Boosty subscribers of a certain level also get access to a private Architecture Community. Big thanks to Nikita, Anatoly, Oleksandr, Dima, Pavel, Robert and Roman for already supporting the newsletter.